Insights, Page 1
Still Sending Endless Emails to Schedule a Meeting?
June 25, 2025
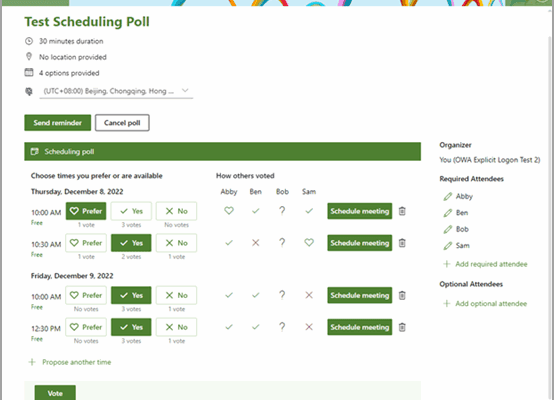
If scheduling a meeting feels like a never-ending email thread or a 15-minute search through calendars, there’s a better way. Instead of relying on the phrase, “Just let me know what works… Read more
Maximize your Microsoft 365 investment
May 28, 2025
If you’re only using Microsoft 365 for email and excel documents, you’re likely overlooking tools you already have and might even be paying extra for elsewhere. Tools like OneDrive, Microsoft Teams, and… Read more
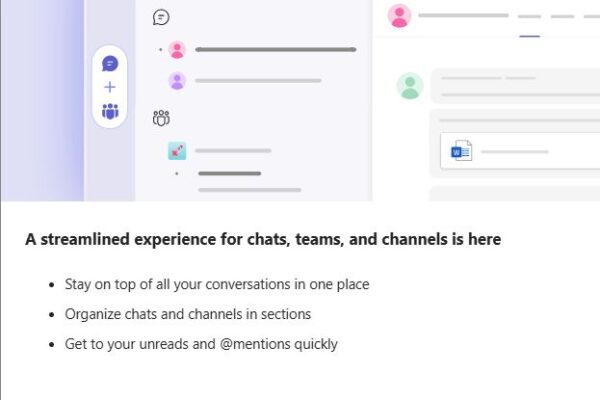
Microsoft Teams streamlined experience for navigating chats, teams, and channels
April 23, 2025
Microsoft Teams Just Got an Upgrade: Here’s What Leaders Need to Know A new feature update quietly rolled out in Microsoft Teams and it could be a welcome change for busy teams… Read more
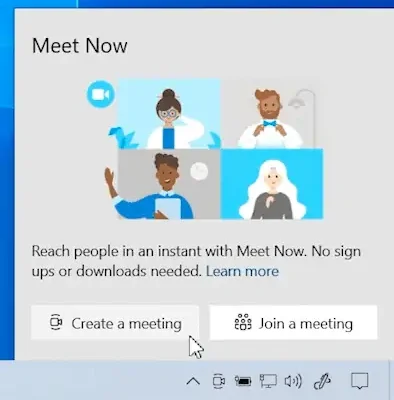
Try the Meet Now feature in Microsoft Teams!
April 16, 2025
Looking to connect on a video call instantly with your team? Try the Meet Now feature in Microsoft Teams! Whether it is a quick catch up, brainstorming session, or impromptu virtual meeting,… Read more
Is your business truly protected 24/7?
March 24, 2025
Is your business truly protected 24/7? A SIEM (Security Information and Event Management) solution is more than just a compliance tool—it’s a crucial asset for business security. ✅ Detect threats early, whether… Read more
Buying business grade devices from a certified partner reseller vs Amazon
March 11, 2025
Why buying business-grade devices from a certified partner reseller vs. Amazon is the best choice. Saving on Amazon might seem like a good idea but you run the risk of ending up… Read more
Anti-Virus Software vs. Endpoint Detection and Response
February 26, 2025
Is your business still relying on outdated anti-virus software security? Traditional antivirus only stops known threats. EDR uses AI and real-time monitoring to detect and stop attacks before they spread, even if… Read more
Microsoft is officially ending support for Windows 10 on October 14, 2025
February 24, 2025
Microsoft is officially ending support for Windows 10 on October 14, 2025. That might seem far off but the time to start planning is now. Here’s why this matters: No more security… Read more
Why is having a hardware refresh strategy in place critical for your business?
November 12, 2024
Why is having a hardware refresh strategy in place critical for your business? A hardware refresh isn’t just about replacing old equipment like servers, desktops, or laptops – it’s about strategically upgrading… Read more